Are you yet to upgrade to Android 4.4 KitKat? Here's something that might give you a bit of encouragement to make the switch: a serious issue with the stock browser on pre-KitKat phones has been discovered, and it could allow malicious websites to access the data of other websites. Sounds scary? Here's what you need to know
The issue - which was first discovered by researcher Rafay Baloch - sees malicious websites being able to inject arbitrary JavaScript into other frames, which could see cookies stolen, or the structure and markup of websites being directly interfered with.
Security researchers are desperately worried by this, with Rapid7 - the makers of the popular security testing framework, Metasploit - describing it as a 'privacy nightmare'. Curious about how it works, why you should be worried, and what you can do about it? Read on for more.
A Basic Security Principle: Bypassed
The basic principle which should prevent this attack from occurring in the first place is called Same Origin Policy. In short, it means that client-side JavaScript running in one website should not be able to be interfere with another website.
This policy has been a foundation of web application security, ever since it was first introduced in 1995 with Netscape Navigator 2. Every single web browser has implemented this policy, as a fundamental security feature, and as a result it is incredibly rare to see such a vulnerability in the wild.
https://www.youtube.com/watch?v=WnjZJ38YEB4
For more information on how SOP works, you may wish to watch the above video. This was taken at an OWASP (Open Web App Security Project) event in Germany, and is one of the best explanations of the protocol I've seen so far.
When a browser is vulnerable to a SOP bypass attack, there's a lot of room for damage. An attacker could feasibly do anything, from use the location API introduced with the HTML5 spec to find out where a victim is located, all the way to stealing cookies.
Fortunately, most browser developers take this kind of attack seriously. Which makes it all the more noteworthy to see such an attack 'in the wild'.
How The Attack Works
So, we know Same Origin Polity is important. And we know that a massive failing of the stock Android browser can potentially lead to attackers circumventing this crucial security measure? But how does it work?
Well, the proof of concept given by Rafay Baloch looks a bit like this:
[NO LONGER AVAILABLE]
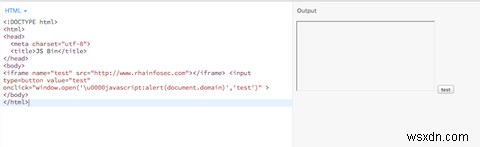
So, what do we have here? Well, there's an iFrame. This is a HTML element that is used to allow websites to embed another web page within another web page. They're not used as much as they used to be, largely because they're an SEO nightmare. However, you still often find them from time to time, and they're still a part of the HTML specification, and have not yet been deprecated.
Following that is a HTML tag representing an input button. This contains some specially crafted JavaScript (notice that trailing '\u0000'?) that, when clicked, outputs the domain name of the current website. However, due to an error in the Android browser, it ends up accessing the attributes of the iFrame, and ends up printing 'rhaininfosec.com' as a JavaScript alert box.
On Google Chrome, Internet Explorer and Firefox, this type of attack would simply error out. It'd (depending on the browser) also produce a log in the JavaScript console informing that the browser blocked the attack. Except, for some reason, the stock browser on pre-Android 4.4 devices does not do that.
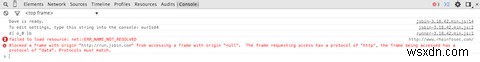
Printing out a domain name isn't terribly spectacular. However, gaining access to cookies and executing arbitrary JavaScript in another website is rather worrying. Thankfully, there's something that can be done.
What Can Be Done?
Users have a few options here. Firstly, stop using the stock Android browser. It's old, it's insecure and there are far more compelling options in the market right now. Google has released Chrome for Android (although, only for devices running Ice Cream Sandwich and up), and there's even mobile variants of Firefox and Opera available.
Firefox Mobile in particular is worth paying attention to. In addition to offering an amazing browsing experience, it also allows you to run applications for Mozilla's own mobile operating system, Firefox OS, as well as install a wealth of awesome add-ons.
https://www.youtube.com/watch?v=zCe_1DxBQDc
If you want to be especially paranoid, there's even a porting of NoScript for Firefox Mobile. Although, it should be noted that most websites are heavily dependent upon JavaScript for rendering client-side niceties, and using NoScript will almost certainly break most websites. This, perhaps, explains why James Bruce described it as part of the 'trifecta of evil'.
Finally, if possible, you'd be encouraged to update your Android browser to the latest version, in addition to installing the latest version of the Android operating system. This ensures that should Google release a fix for this bug further down the line, you are protected.
Although, it's worth noting that there are rumblings that this issue could potentially hit users of Android 4.4 KitKat. However, nothing has emerged that is sufficiently substantial for me to advise readers to switch browsers.
A Major Privacy Bug
Make no mistake, this is a major smartphone security issue. However, by switching to a different browser, you become virtually invulnerable. However, a number of questions remain about the overall security of the Android operating system.
Will you be switching to something a bit more secure, like super-secure iOS or (my favorite) Blackberry 10? Or perhaps will you be staying loyal to Android, and installing a secure ROM like Paranoid Android or Omirom? Or perhaps you're not even that worried.
Let's chat about it. The comments box is below. I can't wait to hear your thoughts.
